Our Cyber Security Approach
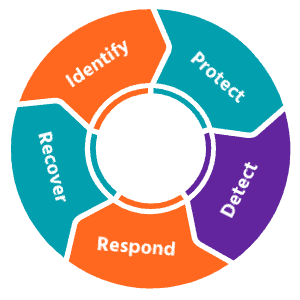
Oxygen Technologies has used the National Institute of Standards and Technology (NIST) Cybersecurity Framework as our template for building our cybersecurity platform for our clients.
Ask us about solutions catalogue to see our solutions and how they integrate into the NIST framework. (we can get really nerdy/cool by creating a matrix of our solutions and our partners and where they fit into the framework.)
In conjunction with the NIST framework, and in partnership with leading vendors like Tenable, Sophos, KnowBe4, Sonicwall, and Cisco, Oxygen has created their own unique cybersecurity ecosystem that ties right into the NIST framework.
Data Resiliency
Our approach to a comprehensive cyber security ecosystem starts with protecting the data. Oxygen adheres to NIST standards for backup & recovery. Your data resiliency requires a comprehensive backup, with test restores done on a predetermined basis. We recommend backing up all data from servers, key workstations and organizations’ cloud platforms, including Microsoft 365. When looking at a solution, ensure you have had a discussion around Recovery Point and Recovery Time Objectives (RPO and RTO) to ensure your backup solution aligns with your business requirements. Finally if your backup solution doesn’t include the term “air-gap”, an immediate discussion with your IT provider is necessary.
End Point Protection and Managed Detection & Response
End-User protection or endpoint security is a crucial aspect of cyber security. After all, it is often an individual (the end-user) who accidentally uploads Malware or another form of cyber threat to their desktop, laptop or mobile device. The foundation of any cyber security ecosystem is protecting your users.
Oxygen utilizes a set of solutions that creates a core ecosystem that include antivirus, anti-spyware, and anti-malware agents. In conjunction, we also deploy DNS filtering that helps protect your client systems, whether they’re behind the corporate firewall, at the coffee shop, or at home.
Sophos MDR is a fully managed 24/7 service delivered by experts who detect and respond to cyberattacks targeting your computers, servers, networks, cloud workloads, email accounts, and more.
Next Generation Firewalls and VPN
Next Generation Firewalls with the appropriate resources and security features are also a foundation of a comprehensive cyber security strategy. Oxygen works with leading vendors to bring best-in-class solutions to the Edge of the Network. In conjunction with a firewall, a Virtual Private Network (VPN,) is also best a practice to secure your branch offices, as well as your users when working remotely.
Multi-Factor Authentication
A username and password combination is no-longer considered adequate protection. Exclusively using simple username and password protection on Internet facing portals such as Webmail, VPN, and Remote Desktop, allow hackers to gain access via weak or stolen user passwords.
Multi-Factor Authentication is a multi-step verification process that adds an extra level of protection by requiring authorization via a mobile device
Ransomware Protection
Ransomware is a form of malware that encrypts all corporate files and prohibits access to this data unless a ransom is paid. Recovery options are to restore from backup (and lose all changes after the last backup) or pay the ransom.
Active protection against ransomware will minimize outbreaks and reduce/eliminate damage.
Vulnerability Assessments
Exploitations in firmware, configurations, and software are a common occurrence in today’s technology. These exploits can make any firm a target both from internal
and external cyber-attacks. Scheduled automated vulnerability scans will verify the security of all servers, network devices, workstations, and laptops on the corporate network.
The scans run on a quarterly basis to check devices for any known exploits. From the scans, a report is created identifying potential risks. Once identified, these risks can be addressed.
Log Aggregation
All network devices and servers generate diagnostic and informational logs for all events that occur. These logs are generally hard to review because they exist in many locations on several different platform types.
With Log Aggregation a centralized device captures all logs generated by configured systems and places them into a single container which can then be used to automate alerts based on specific events. This process allows for greater speed to response when the first signs of trouble begin to appear.
Security Training
In order to increase employee awareness against cyber security threats and social engineering attacks, management must provide training to users. Security training via interactive web modules provide the necessary tools to ensure compliance with policies and procedures.
Security courses can be customized and progress can be tracked to ensure all employees have the appropriate knowledge to assess and mitigate cyber threats.
Hard Drive Encryption
Remote computing has many advantages, however it puts data at risk if a laptop is lost or stolen. Even with a password protected device, laptop hard drives can have their data read and stolen with little effort.
By utilizing hard disk encryption, all data on a laptop hard drive is protected from extraction by an unwanted party.
Active Directory Monitoring
Active Directory administrator accounts should be kept to a bare minimum. With active domain monitoring alerts will be generated any time an account is granted administrative privilege, whether intentional or malicious.
Phishing Test
91% of successful data breaches are started with a spear phishing attack. The best defense for these attacks is to raise employee awareness and improve their security behavior.
“Disguised” phishing emails sent to all users on a quarterly basis will output to a report outlining which users are most susceptible to attacks.
Dark Web Scans
Over 14.7 billion data records have been lost or stolen since 2013 due to data breaches. This data includes account passwords and logon information. Actively monitoring these large data breaches will identify which employee accounts have been leaked and require immediate attention.
Password Vulnerability Testing
Weak passwords are easily compromised via brute force and dictionary attacks. Periodic hash testing against all accounts will expose weak passwords and output reports on which should be immediately changed.
Security Posture Review
Oxygen has implemented it’s own leading edge Security Posture Review (SPR) that takes Oxygen’s Cyber Security solution set and tests our clients and prospective clients current environments against industry best practices. Oxygen has performed over 30 SPRs in 2021, remediating over 200 potential security challenges.
How can we help?
Book a complimentary, no obligation consultation with one of Oxygen’s IT Security Specialists to ensure that both your data and organziation is protected
Book a Complimentary Assessment
See what we’re saying about Cyber Security
-
Ransomware: Get a Breath of Fresh Air
Lorem ipsum dolor sit amet, conse ctetuer adipiscing elit, sed diam nonum nibhie euismod. Facilisis at vero eros et accumsan est iusto
-
SonicWall SWARM Evaluation Assessment
Lorem ipsum dolor sit amet, conse ctetuer adipiscing elit, sed diam nonum nibhie euismod. Facilisis at vero eros et accumsan et iusto odio dignissim qui blandit praesent luptatum zzril delenit augue duis dolore te feugait nulla facilisi. Nam liber tempor
-
Whitepaper: Improve Threat Analysis with Cisco Umbrella and AMP Threat Grid
Lorem ipsum dolor sit amet, conse ctetuer adipiscing elit, sed diam nonum nibhie euismod. Facilisis at vero eros et accumsan est iusto

